Supermicro 、エンタープライズコンピューティング、ストレージ、ネットワーク、グリーンコンピューティング技術におけるグローバルSupermicro、製品のセキュリティ更新情報および情報を提供する確立された情報源です。当社はセキュリティ対策の継続的な改善に努めております。
お客様のセキュリティは最優先事項であり、Supermicro 運用を保護するための対策を講じております。 現代のサーバーおよびストレージシステムは、多様性を増す一方で、セキュリティ確保の必要性からより複雑化しております。脅威の発生に伴い、Supermicro ユーザーとお客様を保護するための防御メカニズムSupermicro 、業界最高水準のセキュリティ知識を提供Supermicro 。Supermicro 、お客様が高水準のセキュリティ基準を満たす製品の導入を期待されていることをSupermicro 。そのため、当社の対応は最高レベルの保護を実現するよう設計されております。
Supermicro 、セキュリティのベストプラクティスに従うことをSupermicro 。これには、オペレーティングシステムを最新の状態に保つこと、最新のファームウェアおよびすべてのソフトウェアを実行することが含まれます。
ライフサイクル・サイバーセキュリティ製品保護
Supermicro 、米国で独占製造された3種類のサーバーSupermicro 。米国工場での製造を一元化することで、システムの完全性が維持されます。これらの「米国製造」製品は、外国によるサイバーセキュリティ侵害の機会を減らし、世界中の顧客様にご利用いただけます。本プログラムの詳細については、「米国製造ソリューション」ページをご覧ください。
Supermicro 、サプライチェーンシステム全体においてサイバーセキュリティSupermicro 管理しております。具体的には、調達・生産段階から運用、そして製品の寿命終了に至るまで、より広範な「製造から廃棄までの全工程」にわたり製品の安全性を確保する取り組みを実施しております。
SupermicroクSupermicro、豊富なセキュリティ機能と特長によって支えられた製品セキュリティ要件を満たすよう設計されております。これらの特長により、Supermicro製品が業界のセキュリティ基準を満たしていることをお客様にご安心いただけます。
最終更新日
Supermicro 、お客様のデータセンターのセキュリティを最優先事項とSupermicro Supermicro 。Supermicro 、新たにリリースされた X14/H14 ならびに X13/H13ならびにX12/H12シリーズのサーバーおよびストレージシステムにも搭載されております。これらの組み込み機能は、データセンター内における安全な運用体制を構築するための指針となります。下記のリストをご確認ください。
| カテゴリー | セキュリティ仕様 | インテル X14 製品 | AMD H14製品 | インテル X13 製品 | AMD H13製品 | インテル X12 製品 | AMD H12製品 |
|---|---|---|---|---|---|---|---|
| ハードウェア | 信頼のシリコン・ルート | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| シャーシ侵入保護 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| トラステッド・プラットフォーム・モジュール(TPM)2.0 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| BMCTPM1 | ✔ | ✔ | ✔ | ✔ | |||
| インテルブートガード | ✔ | ✔ | ✔ | ||||
| インテル® ソフトウェア・ガード・エクステンション(インテル® SGX)1 | ✔ | ✔ | ✔ | ||||
| AMD セキュア・プロセッサ | ✔ | ✔ | ✔ | ||||
| AMD セキュア・メモリー・エンクリプション(SME) | ✔ | ✔ | ✔ | ||||
| AMD セキュア暗号化仮想化(SEV) | ✔ | ✔ | ✔ | ||||
| BIOS/BMC | セキュアブート | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 安全なドライブ消去 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| セキュアフラッシュ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| セキュアなファームウェア・アップデート | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 暗号署名付きファームウェア | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| セキュアなRedfish API3 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| パスワードのセキュリティ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| USBダイナミックイネーブル/ディセーブル | ✔ | ✔ | |||||
| HDDパスワード | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| BMC固有パスワード | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 自動ファームウェアリカバリ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| アンチロールバック | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| ランタイム BMC プロテクション | ✔ | ✔ | ✔ | ✔ | |||
| システム・ロックダウン | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| サプライチェーンのセキュリティ遠隔認証 | ✔ | ✔ | ✔ | ✔ | |||
| ドライブキー管理(スーパーガーディアンズ) | ✔ | ✔ | ✔ | ✔ | |||
| IPMI 2.0ユーザーロック | ✔ | ✔ | ✔ | ✔ | |||
| セキュリティ状態の監視 | ✔ | ✔ | ✔ | ✔ | |||
| セキュリティ・プロトコルおよびデータ・モデル(SPDM)管理2 | ✔ | ✔ | ✔ | ✔ | |||
| 規格 | NIST SP 800-193 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| NIST SP 800-147b | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| NIST SP 800-88 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
注意事項
- 一部の機能は、すべての製品に適用されるわけではありません。
- 1一部のモデルおよび構成について
- 22024年第4四半期を予定
- 3TLS v1.2 / v1.3対応。RMCP+ 暗号スイート3 / 17 対応
ベースボード管理コントローラ(BMC)は、ネットワークの異なる場所にいる複数のユーザーにリモートアクセスを提供します。BMCにより、システム管理者はシステムの健全性を監視し、リモートでコンピュータイベントを管理することができます。BMCは、IPMI管理ユーティリティ(Intelligent Platform Management Interface)とともに使用され、サーバーを集中的に制御および監視することができます。BMCは、お客様の要件に対応する幅広いセキュリティ機能を備えています。

データセンターでBMC機能を有効にしたサーバーを管理するためのセキュリティ・ベスト・プラクティス
認証プロセスを活用した動的システム検証
システム認証を使用したハードウェアとファームウェアの変更の検出
暗号署名されたBMCファームウェア
BMC ファームウェアおよび BIOS に暗号署名するセキュリティ機能について説明します。
BMC独自のパスワードセキュリティ機能
BMC Unique Passwordのメリットについてご紹介します。
AMD 情報AMD、2026年2月
Supermicro 、ゲスト仮想マシン(VM)がホストシステムのクラッシュを引き起こす可能性のあるセキュリティ上の問題についてSupermicro 。AMD 脆弱性に対する緩和策をAMD 。本脆弱性は、Supermicro 、H12、H13、およびH14製品におけるBIOSに影響を及ぼします。
- 31364
インテル プラットフォーム アップデート (IPU) アップデート 2026.1、2026年2月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、X13、X14 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-01314 – 2025.4 IPU - インテル® TDX モジュールに関するお知らせ
- INTEL-SA-01315 – 2026.1 IPU - インテル® チップセット ファームウェア アドバイザリ
- INTEL-SA-01396 – 2026.1 IPU - インテル® プロセッサー ファームウェア アドバイザリ
- INTEL-SA-01397 – 2026.1 IPU - Intel® Trust Domain Extensions (Intel® TDX) モジュール アドバイザリ
AMD 情報AMD、2026年2月
Supermicro 、AMD プロセッサープラットフォームにおける潜在的な脆弱性についてSupermicro 。この脆弱性は、I/Oメモリ管理ユニット(IOMMU)、AMD -セキュアネステッドペーシング(SEV-SNP)、およびその他のプラットフォームコンポーネントに影響を及ぼすものであり、社内および第三者による監査の過程で発見されました。本脆弱性は、Supermicro 、H12、H13、およびH14製品におけるBIOSに影響を及ぼします。
- CVE-2025-52533、CVE-2025-29950、CVE-2024-36355、CVE-2025-29939、CVE-2025-0012、CVE-2025-52536、CVE-2024-21961、 CVE-2025-29948、CVE-2024-21953、CVE-2025-29952、CVE-2025-52534、CVE-2025-54514、CVE-2025-48517、 CVE-2025-0031、CVE-2024-36310、CVE-2025-29946、CVE-2025-48514、CVE-2025-0029、CVE-2025-48509
マイクロソフト セキュア ブート認証局 2011 年 サポート終了のお知らせ:2023 年発行証明書への移行について
マイクロソフトのセキュアブート認証局(CA)2011年発行証明書は2026年6月に失効いたします。これ以降、当該証明書のみに依存しているデバイスでは、Windowsブートマネージャーおよびセキュアブートコンポーネント向けのセキュリティ更新プログラムの提供が停止され、ブートキットによる脆弱性のリスクが高まる可能性があります。 マイクロソフトは新しい2023年証明書への移行を進めております。Supermicro 対応するBIOS更新プログラムSupermicro 、ユーザーの皆様はセキュアブートを有効にしたまま、最新のBIOS/ファームウェアをインストールし、すべての更新を適用されることをお勧めいたします。サポート対象デバイスでは移行が自動的に行われるため、ほとんどのシステムでは直ちに対応する必要はありません。
詳細を見るSupermicro ファームウェアの脆弱性(2026年1月)
Supermicro 、複数のセキュリティ上の問題が発見されました。これらの問題はSupermicroSupermicro を及ぼします。
- 12006
- 12007
AMD 情報AMD、2026年1月
Supermicro 、古いRLBエントリにより、セキュアネステッドペイジング(SNP)が有効な仮想中央処理装置(vCPU)が他の仮想マシン(VM)のTLBエントリを再利用する可能性があり、データの完全性が損なわれる恐れがあるセキュリティ問題Supermicro 。AMD 脆弱性に対する緩和策をAMD 。本脆弱性は、Supermicro に影響を及ぼします。
- 29943
Supermicro ファームウェアの脆弱性、2025年11月
supermicro 、4つのセキュリティ上の問題が発見されました。これらの問題は、Supermicro を及ぼす可能性があります。
- 7623
- 8076
- 8404
- 8727
AMD セキュリティ情報AMD、2025 年 11 月
Supermicro 、古いRLBエントリ(Stale RLB Entry)の問題により、セキュアネステッドペイジング(SNP)が有効な仮想中央処理装置(vCPU)が他の仮想マシン(VM)のTLBエントリを再利用する可能性があり、データの完全性が損なわれる恐れがあるセキュリティ問題をSupermicro 。AMD に対する緩和策をAMD 。本脆弱性は、Supermicro 、H13、およびH14製品におけるBIOSに影響を及ぼします。
- 29934
Supermicro ファームウェアの脆弱性(2025年10月)
Supermicro 、複数のセキュリティ上の問題が発見されました。これらの問題はSupermicroSupermicro を及ぼします。
- 7704
AMD セキュリティ情報AMD、2025年10月
Supermicro 、RDSEED命令がランダム性とは一致しない頻度で「0」を返す可能性があるセキュリティ上の問題をSupermicro 。この問題は、誤って成功(CF=1)を通知し、失敗を成功と誤分類する可能性を示唆しております。AMD 脆弱性に対する緩和策をAMD 。本脆弱性は、Supermicro を及ぼします。
- 62626
AMD セキュリティ情報AMD、2025年10月
Supermicro 、悪意のあるハイパーバイザーがセキュア・ネステッド・ペイジング(SNP)の初期化中にリバースマップテーブル(RMP)を破損する可能性のあるセキュリティ上の問題をSupermicro 。この問題は、AMD 第3世代、第4世代、および第5世代プロセッサーに影響を及ぼします。また、この脆弱性は、Supermicro 、H13、およびH14製品におけるBIOSに影響を及ぼします。
- 0033
Supermicro ファームウェアの脆弱性、2025年9月
Supermicro 、複数のセキュリティ上の問題が発見されました。これらの問題はSupermicroSupermicro を及ぼします。
- 7937
- 6198
インテル・プラットフォーム・アップデート(IPU)2025.2 パート2、2025年8月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、X13、X14 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-01245- 2025.2 IPU - インテル® TDX モジュールに関するアドバイザリー
- INTEL-SA-01249- 2025.2 IPU - インテル® プロセッサー・ストリーム・キャッシュに関するアドバイザリー
インテル・プラットフォーム・アップデート(IPU)2025.3、2025年8月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、X13、X14 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-01280- 2025.3 IPU - インテル® チップセット・ファームウェアに関するアドバイザリー
- INTEL-SA-01312- 2025.3 IPU - インテル® TDX モジュールに関するアドバイザリー
- INTEL-SA-01313- 2025.3 IPU - インテル® Xeon® プロセッサー・ファームウェアに関するアドバイザリー
AMD セキュリティ脆弱性、2025年8月
このアップデートは、第1世代/
- AMD-AMD クライアントの脆弱性 - August 2025
- AMD-AMD サーバーの脆弱性 - 2025 年 2 月
AMD セキュリティ情報AMD、2025 年 7 月
Supermicro 、AMD 実行のセキュリティ上の脆弱Supermicro 。AMD 、マイクロソフト®の報告書「Enter, Exit, Page Fault, Leak: Testing Isolation Boundaries for Microarchitectural Leaks」の調査中に、複数のサイドチャネル攻撃AMD 。
- 36348
- 36349
- 36350
- 36357
2025.1 IPU - インテル® プロセッサー アドバイザリ、INTEL-TA-01209、2025 年 6 月
Supermicro 、ローカルオペレーティングシステム経由のユーザー認証を持つ技術的知識のないユーザーが、インテル® PTTファームウェア内のインテル® CSMEおよびインテル® SPS向けファームウェアにおける範囲外読み取りを悪用したサービス拒否攻撃により、可用性(高)に影響を及ぼす可能性のあるセキュリティ脆弱性をSupermicro
- 2884
AMD セキュリティ情報AMD、2025年6月
Supermicro 、特権攻撃者がx86アーキテクチャから暗号コプロセッサ(CCP)レジスタにアクセスする可能性のあるセキュリティ上の脆弱性をSupermicro 。この問題は、AMD 第1世代、第2世代、第3世代プロセッサおよび一部のH11およびH12世代製品に影響を及ぼします。
- 20599
インテル・プラットフォーム・アップデート(IPU)2025.2、2025年5月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、X13、X14 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-01244- 2025.2 IPU - インテル® プロセッサーに関するアドバイザリー
- INTEL-SA-01247- 2025.2 IPU - インテル® プロセッサー間接分岐予測に関するアドバイザリー
2025.1 IPU - インテル® プロセッサー アドバイザリ、INTEL-TA-01153、2025 年 5 月
プロセッサ・イベントまたは予測によって、不正な操作(または不正なデータを含む正しい操作)が一時的に実行され、秘密チャネルを介してデータが公開される可能性があります。間接分岐予測は、強化された IBRS プロパティおよび間接分岐予測バリアによって完全に制約されていない可能性があります。このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、および X13 ファミリーの製品に適用されます。
本脆弱性は、Supermicro を及ぼします。Supermicro 、本アドバイザリに記載されている脆弱性について、いかなる公開情報または悪意のある利用事例もSupermicro 。
- INTEL-SA-01153 - 2025.1 IPU - インテル® プロセッサーに関するアドバイザリー
AMI セキュリティ勧告 AMI-SA-2025003, 2025年3月
Supermicro 、AMIセキュリティアドバイザリ AMI-SA202503 で報告されている BIOS ファームウェアの潜在的な脆弱性についてSupermicro 。Aptio® V には、攻撃者がローカルな手段で Time-of-check Time-of-use (TOCTOU) レースコンディションを引き起こす可能性のある脆弱性が存在します。この脆弱性が悪用されると、任意のコードが実行される恐れがあります。
本脆弱性は、Supermicro を及ぼします。Supermicro 、本アドバイザリに記載されている脆弱性について、いかなる公開情報または悪意のある利用事例もSupermicro 。
- 54084
AMD セキュリティ情報AMD、2025年3月
Supermicro 、Google®より報告された「AMD 検証脆弱性」と呼ばれるセキュリティ問題についてSupermicro 。この脆弱性は署名検証アルゴリズムの弱点に起因するものであり、管理者特権を持つ攻撃者が任意のCPUマイクロコードパッチをロードする可能性が生じます。
- 36347
インテル・プラットフォーム・アップデート(IPU)2025.1、2025年2月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、および X13 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-01139- 2025.1 IPU - UEFI ファームウェアに関する勧告
- INTEL-SA-01152- 2025.1 IPU - インテル® チップセット・ファームウェアに関するアドバイザリ
- INTEL-SA-01213- 2025.1 IPU - インテル® SGX アドバイザリ
- INTEL-SA-01228- 2025.1 IPU - 第13世代および第14世代インテル® Core™ プロセッサーに関するアドバイザリー
AMD セキュリティ脆弱性、2025年2月
このアップデートは、第1世代/
- AMD-AMD クライアントの脆弱性 - 2025 年 2 月
- AMD-AMD サーバーの脆弱性 - 2025 年 2 月
AMD セキュリティ情報AMD、2025年2月
Supermicro 、AMD サポートされているAmdPlatformRasSspSmm UEFIモジュールにおいて、Eclypsiumにより報告されたシステム管理モード(SMM)コールアウトの脆弱性をSupermicro 。この問題は、AMD 第2世代プロセッサおよびH11世代、H12世代の製品に影響を及ぼします。
- 21924
AMD セキュリティ情報AMD、2025年2月
Supermicro 、Quarkslabより報告された2つのセキュリティ脆弱性について認識Supermicro 。これは複数のAMD サポートされているAmdPspP2CmboxV2およびAmdCpmDisplayFeatureSMM UEFIモジュールに存在し、攻撃者がSMM(システム管理モード)内でコードを実行する可能性がございます。この問題は、AMD 第1世代、第2世代、第3世代、第4世代プロセッサおよびH11、H12、H13世代の製品に影響を及ぼします。
- 0179
- 21925
AMD セキュリティ情報AMD、2025 年 2 月
Supermicro 、AMD (SMU)の電源管理ファームウェア(PMFW)におけるセキュリティ上の脆弱性をSupermicro 。この問題は、AMD MI300X H13DSG-OM製品に影響を及ぼします。
- 21927
- 21935
- 21936
AMD セキュリティ情報AMD、2025 年 2 月
Supermicro 、AMD (SMU)の電源管理ファームウェア(PMFW)におけるセキュリティ上の脆弱性をSupermicro 。この問題は、AMD MI300X H13DSG-OM製品に影響を及ぼします。
- 21971
- 20508
AMD セキュリティ情報AMD、2025 年 2 月
Supermicro 、Google®より報告されたセキュリティ上の脆弱性についてSupermicro 。この脆弱性により、管理者特権を持つ攻撃者が署名検証アルゴリズムの弱点を悪用し、任意のCPUマイクロコードパッチをロードする可能性がございます。これにより、機密ゲストに対するSEVベースの保護機能が失われる結果を招く恐れがございます。
- 56161
Supermicro IPMI ファームウェアの脆弱性(2025年1月)
Supermicro 、複数のセキュリティ上の問題が発見されました。これらの問題はSupermicroSupermicro を及ぼします。
- 10237
- 10238
- 10239
AMD セキュリティ情報AMD、2024年12月
Supermicro 、シリアルプレゼンス検出(SPD)メタデータを改変することで、接続されたメモリモジュールを実際よりも大容量に見せかける可能性があり、メモリアドレスのエイリアシングを引き起こす恐れがあるセキュリティ上の問題をSupermicro 。この問題は、AMD 第3世代および第4世代プロセッサーを搭載したマザーボードに影響を及ぼします。また、Supermicro を及ぼします。
- 21944
Supermicro IPMIファームウェアの脆弱性「テラピン」、2024年10月
Supermicro セキュリティ上の問題が発見されました。Terrapin脆弱性により、攻撃者がセキュア署名アルゴリズムをダウングレードし、特定のセキュリティ対策を無効化することが可能となります。Terrapin攻撃には、アクティブな中間者攻撃(Man-in-the-Middle)の実行者が必要です。
- 48795
BIOSの脆弱性、2024年9月
Supermicro BIOSファームウェアに存在する2つの潜在的な脆弱性を認識Supermicro これらの脆弱性により、攻撃者がSMRAMへの書き込みを行い、RIP/EIPを乗っ取る可能性がございます。これらはデンバートンプラットフォームにおけるSupermicro を及ぼします。本アドバイザリに記載されている脆弱性について、Supermicro 公的な発表や悪意のある利用事例はSupermicro
- 8738
- 44075
インテル・プラットフォーム・アップデート(IPU)2024.3、2024年8月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、および X13 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-01038- 2024.2 IPU - インテル® Core™Ultra プロセッサー・ストリーム・キャッシュに関するアドバイザリー
- INTEL-SA-01046- 2024.2 IPU - インテル® プロセッサー・ストリーム・キャッシュに関するアドバイザリー
- INTEL-SA-00999- 2024.3 IPU - インテル® チップセット・ファームウェアに関するアドバイザリー
- INTEL-SA-01083- 2024.3 IPU - SMI 転送モニタに関するアドバイザリ
- INTEL-SA-01100- 2024.3 IPU - インテル® Xeon® プロセッサーに関するアドバイザリー
- INTEL-SA-01118- 2024.3 IPU - 第3世代インテル® Xeon® スケーラブル・プロセッサー アドバイザリー
- INTEL-SA-01103- 2024.3 IPU - インテル® プロセッサー RAPL インターフェースに関するアドバイザリー
AMD セキュリティ脆弱性、2024年8月
このアップデートは、第1/2/3/4世代AMD EPYC™プロセッサーを搭載したH11、H12、H13製品ファミリーに適用されます。このアップデートは、Ryzen™ Threadripper™ プロセッサーを搭載した M11/M12 および H13 製品ファミリーにも適用されます。AMD EPYC™ およびAMD Ryzen™ AGESA™ PI パッケージでは、さまざまなプラットフォーム・コンポーネントに潜在的な脆弱性が発見され、緩和されています。
- AMD-AMD クライアントの脆弱性 - 2024 年 8 月
- AMD-AMD サーバーの脆弱性 - 2024 年 8 月
AMD セキュリティ情報AMD、2024 年 8 月
Supermicro 、SMMロックが有効な場合でも、ルートアクセス権を持つ攻撃者がシステム管理モード(SMM)の設定を変更できるセキュリティ上の脆弱性をSupermicro この問題は、AMD 第1世代、第2世代、第3世代、第4世代プロセッサーおよびH11、H12、H13世代の製品に影響を及ぼします。
- 31315
AMD セキュリティ情報AMD、2024 年 8 月
Supermicro 、悪意のあるハイパーバイザーが、Secure Encrypted Virtualization–Secure Nested Paging(SEV-SNP)ゲスト仮想マシン(VM)のメモリを、そのゲストVMが廃止された後に復号化できる可能性があるというセキュリティ上の問題をSupermicro この問題は、AMD 第3世代および第4世代プロセッサーを搭載したマザーボードに影響を及ぼします。また、この脆弱性は、Supermicro BIOSに影響を及ぼします。
- 31355
- 21978
- 21980
PKFAIL:Supermicro ファームウェアの脆弱性(2024年7月)
Supermicro 、「PKFAIL」として知られるセキュリティ脆弱性問題をSupermicro 。この新たな脆弱性により、悪意のある攻撃者がオペレーティングシステムから高度なファームウェアレベルの脅威を仕掛ける可能性がございます。Supermicro 、BIOSの信頼の基盤(Root of Trust)となるプラットフォームキー(PK)が安全でない状態で使用されていたことが判明いたしました。これらの安全でないキーは、アメリカン・メガトレンド・インターナショナル(AMI)によって生成され、Supermicro参照例として提供されていたものでした。
詳細を見るOpenSSH "regreSSHion" 脆弱性、2024年7月
Supermicro BMCファームウェアにおいて、OpenSSHの重大なシグナルハンドラ競合状態(通称「regreSSHion」)に関連するセキュリティ脆弱性が発見されました。この脆弱性により、認証不要のリモートコード実行(RCE)がルート権限で発生する可能性があります。
- 6387
BIOSの脆弱性、2024年7月
Supermicro 、BIOSファームウェアに潜在的な脆弱性が存在することをSupermicro 。これらの脆弱性は、特定のX11マザーボードに影響を及ぼします。本アドバイザリに記載されている脆弱性について、Supermicro 、これらが公に公表された事例や悪意のある利用事例をSupermicro 。
- 36432
- 36433
- 36434
Supermicro IPMIファームウェアの脆弱性(2024年7月)
Supermicro セキュリティ上の問題が発見されました。この問題は、BMC(Baseboard Management Controller)のウェブサーバーコンポーネントに影響を及ぼします。Supermicro 潜在的な脆弱性は、ファームウェアの「GetValue」関数におけるバッファオーバーフローに起因する可能性があり、これは入力値のチェック不足によって引き起こされるものです。
- 36435
AMD セキュリティ情報AMD、2024年6月
Supermicro 、AMD 潜在的な脆弱性をSupermicro 。この問題は、AMD 第1世代、第2世代、第3世代プロセッサ搭載マザーボードに影響を及ぼします。また、この脆弱性はSupermicro を及ぼします。
- 23829
AMD セキュリティ情報AMD、2024 年 5 月
Supermicro 、サーバーおよびクライアントデスクトップ・モバイル向けAPU/CPUAMD (ドライブ実行環境)ドライバーにおけるメモリリーク脆弱性についてSupermicro 。この脆弱性により、特権ユーザーが機密情報を取得する可能性がございます。AMD 第3世代プロセッサーおよびマザーボードに影響を及ぼします。また、Supermicro 影響が確認されております。
- 20594
- 20597
インテル・プラットフォーム・アップデート(IPU)2024.2、2024年5月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X13 ファミリーに適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-01036- 2024.2 IPU - インテル® TDX モジュール・ソフトウェアに関するアドバイザリー
- INTEL-SA-01051- 2024.2 IPU - インテル® プロセッサーに関するアドバイザリー
- INTEL-SA-01052- 2024.2 IPU - インテル® Core™Ultra プロセッサーに関するアドバイザリー
Supermicro ファームウェアの脆弱性(2024年4月)
Supermicro 、複数のセキュリティ上の脆弱性が発見されました。これらの問題(クロスサイトスクリプティングおよびコマンドインジェクション)は、Supermicro IPMI(Web UI)のWebサーバーコンポーネントに影響を及ぼす可能性があります。これらの潜在的な脆弱性を軽減するため、更新されたBMCファームウェアが作成されました。
- SMC-2024010010(CVE:CVE-2024-36430)
- SMC-2024010011(CVE:CVE-2024-36431)
- SMC-2024010012(CVE:CVE-2023-33413)
インテル® プラットフォーム・アップデート (IPU) 2024.1 および INTEL-TA-00986、2024 年 3 月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、および X13 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00898- 2024.1 IPU - インテル® Atom® プロセッサーに関するアドバイザリー
- INTEL-SA-00923- 2024.1 IPU - インテル® チップセット・ソフトウェアおよび SPS アドバイザリ
- INTEL-SA-00929- 2024.1 IPU - BIOS アドバイザリ
- INTEL-SA-00950- 2024.1 IPU OOB - インテル® プロセッサーに関するアドバイザリー
- INTEL-SA-00960- 2024.1 IPU - インテル® Xeon® プロセッサーに関するアドバイザリー
- INTEL-SA-00972- 2024.1 IPU - インテル® プロセッサー・バス・ロックに関するアドバイザリー
- INTEL-SA-00982- 2024.1 IPU - インテル® プロセッサー・リターン予測アドバイザリー
- INTEL-SA-00986- 第4世代インテル® Xeon® プロセッサーに関するアドバイザリー
- INTEL-SA-01045- 2024.1 IPU OOB - インテル® Xeon® D プロセッサーに関するアドバイザリー
AMD セキュリティ情報AMD、2024 年 2 月
Supermicro 、AMD についてSupermicro 。この問題は、AMD 第1世代、AMD 第2世代、AMD 第3世代および第4世代プロセッサに影響を及ぼします。この脆弱性は、Supermicro 、H12、および特定モデルのH13マザーボードに影響を及ぼします。
- 20576
- 20577
- 20579
- 20587
AMD セキュリティ情報AMD、2024 年 2 月
Supermicro 、SEV-SNPファームウェアの脆弱性についてSupermicro 。この問題は、AMD 第3世代および第4世代プロセッサーに影響を及ぼします。本脆弱性は、Supermicro を及ぼします。
- 31346
- 31347
PixieFAILの脆弱性、2024年1月
Supermicro 、BIOSファームウェアにおける「PixieFAIL」と呼ばれる潜在的な脆弱性をSupermicro 。UEFIのオープンソース実装であるTianocore EDKIIのTCP/IPスタック(NetworkPkg)において、複数の脆弱性が発見されました。これらの9つの脆弱性は、ネットワーク経由で悪用された場合、リモートコード実行、DoS攻撃、DNSキャッシュポイズニング、および機密情報の漏洩につながる可能性があります。 PixieFAILは、特定のX11、X12、H11、H12、H13、およびR12製品におけるSupermicro を及ぼします。Supermicro 、本アドバイザリに記載されているこれらの脆弱性に関する公開情報または悪意のある利用事例をSupermicro 。
- 45229
- 45230
- 45231
- 45232
- 45233
- 45234
- 45235
- 45236
- 45237
ロゴFAILの脆弱性、2023年12月
Supermicro 、BIOSファームウェアに「LogoFAIL」と呼ばれる潜在的な脆弱性が存在することを認識Supermicro 。 BIOSで使用される画像解析ライブラリにおける入力検証の不備により、特権ユーザーがローカルアクセスを通じて特権昇格を可能にする恐れがあります。LogoFAILは、特定のX11、X12、X13、H11、M12、Supermicro R12製品におけるSupermicro を及ぼします。Supermicro 、本勧告に記載されている脆弱性に関する公的な発表や悪意のある利用事例をSupermicro 。
- 39538
- 39539
Supermicro IPMIファームウェアの脆弱性(2023年12月)
- CVE-2023-33411: IPMI BMC SSDP/UPnP ウェブサーバディレクトリトラバーサルおよび iKVM アクセスによる BIOS 再起動許可
- CVE-2023-33412: IPMI BMC 管理用ウェブインターフェイスの仮想フロッピー/USB リモートコマンド実行
- CVE-2023-33413: IPMI BMC デバイスはハードコードされた設定ファイル暗号化キーを使用しており、攻撃者は悪意のある設定ファイルパッケージを作成してアップロードし、リモートでコマンドを実行することができます。
AMD セキュリティ情報AMD
Supermicro 、AMD 脆弱性をSupermicro 。この問題は、AMD (SEVおよびSEV-ES)、AMD (SEVおよびSEV-ES)、AMD (SEV、SEV-ES、SEV-SNP)に影響を及ぼします。 この脆弱性は、Supermicro H11およびH12マザーボードに影響を及ぼします。
- 20592
インテル® プラットフォーム・アップデート (IPU) 2023.4 および INTEL-SA-00950 (2023年11月)
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、および X13 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00924- 2023.4 IPU - BIOS アドバイザリ
- INTEL-SA-00950- インテル® プロセッサーに関するアドバイザリー
AMD セキュリティ脆弱性、2023年11月
このアップデートは、第1世代/
- AMD-AMD クライアントの脆弱性 - 2023 年 11 月
- AMD-AMD サーバーの脆弱性 - 2023 年 11 月
Supermicro IPMIファームウェアの脆弱性
Supermicro 、複数のセキュリティ上の脆弱性が発見されました。これらの問題(クロスサイトスクリプティングおよびコマンドインジェクション)は、Supermicro IPMI(Web UI)のWebサーバーコンポーネントに影響を及ぼす可能性があります。これらの潜在的な脆弱性を軽減するため、更新されたBMCファームウェアが作成されました。
- 40289
- 40284
- 40287
- 40288
- 40290
- 40285
- 40286
スタックオーバーフローによる変数の変更
Supermicro 潜在的な脆弱性が発見されました。Supermicro 、変数を操作することで制御フローを乗っ取る可能性があり、カーネルレベル特権を持つ攻撃者が特権を昇格させ、任意のコードを実行する可能性が生じます。
- 34853
AMD セキュリティ情報AMD
Supermicro 、リターンアドレス予測問題(別名「INCEPTION」)についてSupermicro この問題は、AMD 第3世代および第4世代プロセッサーに影響を及ぼします。本脆弱性は、Supermicro を及ぼします。
- 20569
インテル・プラットフォーム・アップデート(IPU)2023.3、2023年8月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、および X13 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00783- 2023.2 IPU - インテル® チップセット・ファームウェアに関するアドバイザリー
- INTEL-SA-00813- 2023.2 IPU - BIOS アドバイザリ
- INTEL-SA-00828- 2023.2 IPU - インテル® プロセッサーに関するアドバイザリー
- INTEL-SA-00836- 2023.2 IPU - インテル® Xeon® スケーラブル・プロセッサーに関するアドバイザリー
- INTEL-SA-00837- 2023.2 IPU - インテル® Xeon® プロセッサーに関するアドバイザリー
AMD セキュリティ情報AMD
Supermicro 、クロスプロセス情報漏洩(通称「Zenbleed」)Supermicro 。この問題は、AMD 7002 プロセッサ(別名AMD 2」プロセッサ)に影響を及ぼします。本脆弱性は、Supermicro 。
- 20593
SMTP通知におけるシェルインジェクション
supermicro 存在する脆弱性は、SMTP通知設定に影響を及ぼす可能性があります。この脆弱性により、認証されていない悪意のある攻撃者が、アラート設定の件名などのユーザー入力を操作できる恐れがあり、その結果、任意のコードが実行される可能性があります。
- 35861
サービス・ロケーション・プロトコルSLPにおける反射型サービス拒否(DoS)増幅脆弱性
Service Location Protocol (SLP) は、認証されていないリモートの攻撃者が任意のサービスを登録することを可能にします。これにより、攻撃者はなりすましの UDP トラフィックを使用して、大幅な増幅率でサービス拒否 (DoS) 攻撃を行うことができます。
- 29552
メディア情報Intel BootGuard OEM 秘密鍵が漏洩した可能性、2023 年 5 月
Supermicro 秘密鍵をSupermicro および使用する方法を分析した結果、Supermicro 影響を受けません。
インテル・プラットフォーム・アップデート(IPU)2023.2、2023年5月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、および X13 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00807- 2023.2 IPU - BIOS アドバイザリ
AMD セキュリティ脆弱性、2023年5月
このアップデートは、第1/2/3/4世代AMD EPYC™プロセッサーを搭載したH11、H12、H13製品ファミリーに適用されます。このアップデートは、Ryzen™ Threadripper™ プロセッサーを搭載した M12 製品ファミリーにも適用されます。AMD EPYC™ およびAMD Ryzen™ AGESA™ PI パッケージでは、さまざまなプラットフォーム・コンポーネントに潜在的な脆弱性が発見され、緩和されています。
- AMD-AMD クライアントの脆弱性 - 2023年5月
- AMD-AMD サーバーの脆弱性 - 2023 年 5 月
スーパードクター5 アドバイザリー、2023年3月
研究者により、Supermicro (SD5)に脆弱性が確認されました。この脆弱性により、Webインターフェース上で認証された任意のユーザーが、SuperDoctor5(SD5)がインストールされているシステム上で、リモートから任意のコマンドを実行できる可能性があります。
- 26795
インテル・プラットフォーム・アップデート(IPU)2023.1、2023年2月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11、X12、および X13 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00700- 2023.1 IPU - インテル® Atom® およびインテル® Xeon® スケーラブル・プロセッサー アドバイザリ
- INTEL-SA-00717- 2023.1 IPU - BIOS アドバイザリ
- INTEL-SA-00718- 2023.1 IPU - インテル® チップセット・ファームウェアに関するアドバイザリー
- INTEL-SA-00730- 2023.1 IPU - 第3世代インテル® Xeon® スケーラブル・プロセッサー アドバイザリー
- INTEL-SA-00738- 2023.1 IPU - インテル® Xeon® プロセッサーに関するアドバイザリー
- INTEL-SA-00767- 2023.1 IPU - インテル® プロセッサーに関するアドバイザリー
電圧レギュレータ・モジュール(VRM)と集積回路間(I²C)の過電圧/低電圧化、2023年1月
研究者は、ボード・マネージメント・コントローラー(BMC)の脆弱性を特定しました。この脆弱性は、CPUの指定された動作範囲外で電圧を変更することを可能にし、その結果、正常な計算に影響を及ぼす可能性があります。
- 43309
AMD セキュリティ脆弱性、2023年1月
このアップデートは、第1/2/3/4世代AMD EPYC™プロセッサーを搭載したH11およびH12製品ファミリーに適用されます。このアップデートは、Ryzen™ Threadripper™ プロセッサーを搭載した M12 ファミリーの製品にも適用されます。AMD EPYC™ およびAMD Ryzen™ AGESA™ PI パッケージでは、さまざまなプラットフォーム・コンポーネントに潜在的な脆弱性が発見され、緩和されています。
- AMD-AMD クライアントの脆弱性 - 2023 年 1 月
- AMD-AMD サーバーの脆弱性 - 2023 年 1 月
インテル・プラットフォーム・アップデート(IPU)2022.3、2022年11月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11 および X12 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00610- 2022.3 IPU - インテル® チップセット・ファームウェアに関するアドバイザリー
- INTEL-SA-00668- 2022.2 IPU - BIOS アドバイザリ
OpenSSLアドバイザリー、2022年11月
OpenSSLのバージョン3.xから3.0.6までにおいて、深刻度の高いセキュリティ脆弱性が確認されました。この脆弱性により、クラッシュや予期せぬ動作が発生する可能性があります。Supermicro 、このOpenSSLの脆弱性の影響を受けません。
- 3786
- 3602
2022年8月、Microsoft Windowsのセキュアブートバイパス
研究者は、x64 UEFIセキュアブートを使用しているすべてのコンピュータシステムに影響を与える可能性のある、マイクロソフト社のサードパーティ製ブートローダーの複数の脆弱性を特定しました。
- 34301
- 34302
- 34303
インテル・プラットフォーム・アップデート(IPU)2022.2、2022年8月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X11 および X12 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00657- 2022.2 IPU - インテル® プロセッサーに関するアドバイザリー
- INTEL-SA-00669- 2022.2 IPU - インテル® チップセット・ファームウェアに関するアドバイザリー
- INTEL-SA-00686- 2022.2 IPU - BIOS アドバイザリ
インテル・プラットフォーム・アップデート(IPU Update)2022.1、2022年6月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X10、X11、および X12 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00601- 2022.1 IPU - BIOS アドバイザリ
- INTEL-SA-00613- 2022.1 IPU - インテル® Boot Guard およびインテル® TXT アドバイザリー
- INTEL-SA-00614- 2022.1 IPU - インテル® SGX アドバイザリ
- INTEL-SA-00615- 2022.1 IPU - インテル® プロセッサー MMIO Stale Data アドバイザリ
- INTEL-SA-00616- 2022.1 IPU - インテル®Xeon アドバイザリ
- INTEL-SA-00617- 2022.1 IPU - インテル® プロセッサーに関するアドバイザリー
AMD セキュリティ脆弱性、2022年5月
このアップデートは、第1/2/3世代AMD EPYC™プロセッサーを搭載したH11およびH12製品ファミリーに適用されます。このアップデートは、Ryzen™ Threadripper™ プロセッサーを搭載した M12 ファミリーの製品にも適用されます。AMD EPYC™ およびAMD Ryzen™ AGESA™ PI パッケージにおいて、さまざまなプラットフォームコンポーネントに潜在的な脆弱性が発見され、緩和されています。
- AMD-AMD クライアントの脆弱性 - 2022年5月
- AMD-AMD サーバーの脆弱性 - 2022 年 5 月
インテル・プラットフォーム・アップデート(IPU)2021.2、2022年2月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X10、X11、および X12 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00470- 2021.2 IPU - インテル® チップセット・ファームウェアに関するアドバイザリー
- INTEL-SA-00527- 2021.2 IPU - BIOS アドバイザリ
- INTEL-SA-00532- 2021.2 IPU - インテル® プロセッサーのブレークポイント制御フローに関するアドバイザリー
- INTEL-SA-00561- 2021.2 IPU - インテル® プロセッサーに関するアドバイザリー
- INTEL-SA-00589- 2021.2 IPU - インテル® Atom® プロセッサーに関するアドバイザリー
SupermicroApache Log4j脆弱性への対応
Supermicro 業界と連携し、高優先度のCVE-2021-44228(Apache Log4j 2)問題(通称「Log4Shell」)、CVE-2021-45046(Apache Log4j 2)問題、およびCVE-2021-45105(Apache Log4j 2)の問題についてもSupermicro 。また、Apache Log4j 1.2 に関するCVE-2021-4104およびCVE-2019-17571の問題についてもSupermicro 。
Supermicro の大半は、これら5つの脆弱性の影響を受けません。影響を受けるアプリケーションSupermicro Manager(SPM)のみです。この問題は、Supermicro Manager(SPM)の新バージョンで早急に修正される予定です。SPMにはLog4jバージョン2.17.0が搭載されます。
Log4j 2
- 44228
- 45046
- 45105
Log4j 1.2
- 17571
- 4104
インテル・プラットフォーム・アップデート(IPU)2021.2、2021年11月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X10、X11、および X12 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00528- 2021.2 IPU - インテル® Atom® プロセッサーに関するアドバイザリー
- INTEL-SA-00562- 2021.1 IPU - BIOS 参照コードに関するアドバイザリ
AMD セキュリティ脆弱性、2021年11月
このアップデートは、第1/2/3世代AMD EPYC™ プロセッサーを搭載した H11 および H12 ファミリーの製品に適用されます。さまざまなプラットフォーム・コンポーネントに潜在的な脆弱性が発見され、AMD EPYC™ AGESA™ PI パッケージで緩和されています。
- AMD-AMD サーバーの脆弱性 - 2021 年 11 月
インテル セキュリティ アドバイザリ Intel-SA-00525(2021 年 7 月
- INTEL-SA-00525- インテル BSSA (BIOS 共有 SW アーキテクチャ) DFT アドバイザリ
Intel-SA-00525 セキュリティアドバイザリは、Supermicro には影響いたしません。
詳細を見るインテル・プラットフォーム・アップデート(IPU)2021.1、2021年6月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X10、X11、および X12 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00442- 2021.1 IPU - Intel VT-d アドバイザリ
- INTEL-SA-00459- 2021.1 IPU - Intel-CSME-SPS-TXE-DAL-AMT-Advisory
- INTEL-SA-00463- 2021.1 IPU - BIOS アドバイザリ
- INTEL-SA-00464- 2021.1 IPU - インテル プロセッサーに関するアドバイザリー
- INTEL-SA-00465- 2021.1 IPU - インテル プロセッサー アドバイザリ
Supermicro(2021年3月)
Supermicro 、X10 UPマザーボードの一部モデルにおいてのみ確認されているTrickboot問題について認識Supermicro 。Supermicro 、この脆弱性に対する緩和策を提供Supermicro 。
TrickBootは、TrickBotマルウェアツールセットの新機能で、脆弱性を発見し、攻撃者がデバイスのBIOSを読み書き/消去できるようにします。
続きを読むBIOSがLinux OSのGRUB2ブートローダーの脆弱性を検出、2020年11月
バージョン 2.06 より前の GRUB2 に欠陥が見つかりました。攻撃者は GRUB2 の欠陥を利用して GRUB 検証プロセスを乗っ取り、改ざんする可能性があります。BIOS はこの状態を検出し、エラーメッセージとともにブートを停止します。
- 10713
インテル・プラットフォーム・アップデート(IPU)2020.2、2020年11月
このアップデートは、インテル® Xeon® およびその他のインテル® プロセッサーを搭載した X10、X11、および X12 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- INTEL-SA-00358- 2020.2 IPU - BIOS アドバイザリ
- INTEL-SA-00391- 2020.2 IPU - インテル® CSME、SPS、TXE、および AMT アドバイザリ
- INTEL-SA-00389- 2020.2 IPU - インテル® RAPL アドバイザリ
- INTEL-SA-00390- インテル BIOS プラットフォームサンプルコードアドバイザリー
インテル月例セキュリティ・アップデート(2020年9月
このアップデートは、インテル® Core® プロセッサーを搭載した X11 および X12 ファミリーの製品に適用されます。インテル® 9 月セキュリティー・アップデートは、これまで個別に提供されていたセキュリティー・アップデートを統合したものです。
なお、X10シリーズにつきましては、今回の発表による影響はございません。
- インテル-SA-00404- インテル® AMT およびインテル® ISM アドバイザリー
インテル・プラットフォーム・アップデート(IPU)2020.1、2020年6月
このアップデートは、インテル® Xeon® プロセッサーを搭載した X10 および X11 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- インテル® CSME、SPS、TXE、AMT および DAL に関するアドバイザリー
- Intel-SA-00320- スペシャルレジスタバッファのデータサンプリングに関するアドバイザリー
- Intel-SA-00322- 2020.1 IPU BIOS アドバイザリ
- インテル-SA-00329- インテル® プロセッサーのデータ漏洩に関するアドバイザリー
- インテル-SA-00260- (更新) インテル® プロセッサー・グラフィックス 2019.2 QSR アップデートに関するアドバイザリー
ErP(エコデザイン)適合のロット9
ロット9規制は、エンタープライズレベルのサーバーなどのデータストレージデバイスを対象とした新たな製品基準です。Supermicro ロット9準拠の一環として、サーバーおよびストレージ製品における欧州連合(EU)のエコデザイン要件をどのようにSupermicro ご説明いたします。
詳細を見るインテル2020年2月月例セキュリティ・アップデート
このアップデートは、インテル® Core® プロセッサーを搭載した X11 ファミリーの製品に適用されます。月例インテル® 2 月セキュリティー・アップデートは、これまで個別に提供されていたセキュリティー・アップデートを統合したものです。
- Intel-SA-00307- 権限昇格、サービス拒否、情報開示
インテル月例セキュリティ・アップデート(2019年12月
このアップデートは、インテル® Xeon® プロセッサーを搭載した X10 および X11 ファミリーの製品に適用されます。インテル 12 月セキュリティー・アップデートは、これまで個別に提供されていたセキュリティー・アップデートを統合したものです。
- インテル-SA-00289- インテル® プロセッサー電圧設定の変更に関するアドバイザリー
- Intel-SA-00317- 仮想化環境における予期しないページフォルトに関するアドバイザリー
インテル・プラットフォーム・アップデート(IPU Update)2019.2、2019年11月
このアップデートは、インテル® Xeon® プロセッサーを搭載した X10 および X11 ファミリーの製品に適用されます。インテル® Platform Update (IPU) は、これまで個別に提供されていたセキュリティアップデートを統合したものです。
- Intel-SA-00164- インテル® トラステッド・エグゼキューション・テクノロジー 2019.2 IPU アドバイザリー
- インテル-SA-00219- インテル® SGX 2019.2 インテル® プロセッサー・グラフィックス IPU アップデートに関するアドバイザリー
- インテル-SA-00220- インテル® SGX およびインテル® TXT アドバイザリー
- Intel-SA-00240- Intel CPU Local Privilege Escalation Advisory
- インテル® CSME、サーバー・プラットフォーム・サービス、トラステッド・エグゼキューション・エンジン、インテル® アクティブ・マネジメント・テクノロジーおよびダイナミック・アプリケーション・ローダー 2019.2 IPU アドバイザリー
- インテル-SA-00254- インテル® システム管理モード 2019.2 IPU アドバイザリー
- インテル-SA-00260- インテル® プロセッサー・グラフィックス 2019.2 IPU アドバイザリー
- Intel-SA-00270- TSX トランザクションの非同期中止に関するアドバイザリー
- Intel-SA-00271- 電圧変調に関するテクニカル・アドバイザリー
- Intel-SA-00280- BIOS 2019.2 IPU アドバイザリ
BMC/IPMI セキュリティ脆弱性アップデート 2019年9月3日
研究者により、Supermicro 仮想メディア機能において複数のセキュリティ関連の問題が確認されました。これに対処するためには、BMCファームウェアの更新が必要となります。
CVE-2019-16649
CVE-2019-16650
AMD セキュリティ脆弱性LinuxオペレーティングシステムにおけるSecure Encrypted Virtualization Invalid ECC Curve Points (SEV ECC)の脆弱性
9836
詳細を見るインテル四半期セキュリティリリース(QSR)アップデート2019.1、2019年5月
このアップデートは、インテル® Xeon® プロセッサーを搭載した X8、X9、X10、および X11 ファミリーの製品に適用されます。四半期ごとのセキュリティー・リリース (QSR) は、これまで個別に提供されていたセキュリティー・アップデートをまとめて提供するものです。
- インテル-SA-00213(CVE-2019-0089、CVE-2019-0090、CVE-2019-0086、CVE-2019-0091、CVE-2019-0092、CVE-2019-0093、CVE-2019-0094、CVE-2019-0096、CVE-2019-0097、CVE-2019-0098、CVE-2019-0099、CVE-2019-0153、CVE-2019-0170)
- INTEL-SA-00223BIOSは影響を受けません。
- INTEL-SA-00233(CVE-2018-12126、CVE-2018-12127、CVE-2018-12130、CVE-2019-11091)
これらの問題に対する BIOS アップデートは現在順次リリースされています。影響を受ける製品と必要な BIOS アップデートの詳細については、以下を参照してください。
インテル四半期セキュリティリリース(QSR)アップデート2018.4、2019年3月
このアップデートは、インテル® Xeon® プロセッサーを搭載した X11 ファミリー製品にのみ適用されます。四半期ごとのセキュリティー・リリース (QSR) は、これまで個別に提供されていたセキュリティー・アップデートをまとめて提供するものです。
- インテル-SA-00185(CVE-2018-12188、CVE-2018-12189、CVE-2018-12190、CVE-2018-12191、CVE-2018-12192、CVE-2018-12199、CVE-2018-12198、CVE-2018-12200、CVE-2018-12187、CVE-2018-12196、CVE-2018-12185、CVE-2018-12208)
- インテル-SA-00191(CVE-2018-12201、CVE-2018-12202、CVE-2018-12203、CVE-2018-12205、CVE-2018-12204)
"ネタバレ"インテル・プロセッサーの投機的実行に関する新しい研究論文
詳細を見るスペクターとメルトダウンのサイドチャネル投機的実行
- インテル SA-00115(CVE-2018-3639, CVE-2018-3640)
- Intel-SA-00088(CVE-2017-5715、CVE-2017-5753、CVE-2017-5754)
- Intel-SA-00161(CVE-2018-3615、CVE-2018-3620、CVE-2018-3646)
インテル® マネージメント・エンジン (ME)、インテル® サーバー・プラットフォーム・サービス (SPS)、およびインテル® トラステッド・エグゼキューション・エンジン (TXE) に関するインテル® セキュリティの脆弱性について
- Intel-SA-00086(CVE-2017-5705、CVE-2017-5708、CVE-2017-5711、CVE-2017-5712、CVE-2017-5706、CVE-2017-5709、CVE-2017-5707、CVE-2017-571000)
BIOS/BMCファームウェア 2017年以前のセキュリティアップデート
2017年以前に公表された「一般的な脆弱性と暴露に対するファームウェアの修正」を参照してください。
Supermicro 、セキュリティコミュニティとSupermicro 連携し、当社製品ライン全体のセキュリティを特定し強化してまいります。Supermicro に公開されているCVEへの対応策については、以下をご参照ください。
詳細を見るセキュリティに関するよくある質問カテゴリー "セキュリティ "を選択
製品セキュリティ問題の報告
Supermicro セキュリティ上の問題が発生した場合は、以下の詳細を記載の上、supermicroまでメールをお送りください:
- 製品名/SKU
- 脆弱性に関する詳細レポート
- 複製指示
- 関連するCVE
機密情報や個人情報を明文のメールに記載しないでください。PGPキーを使用してメッセージを暗号化してください。Supermicro ご報告内容を審査し、問題解決のためご連絡いたします。
詳細を見るSupermicroの製品セキュリティ更新情報をご確認ください
本日よりご登録ください
Supermicro アラートを受信するための購読を開始するには、以下の手順をお取りください:
1.画面の右上に移動し、サインインするか、シングルサインオン(SSO)アカウントを作成します:
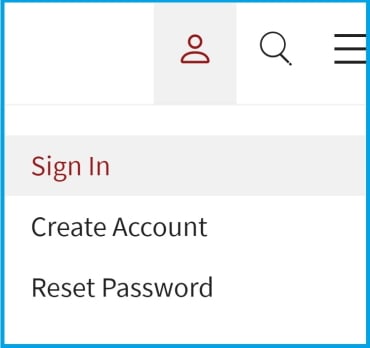
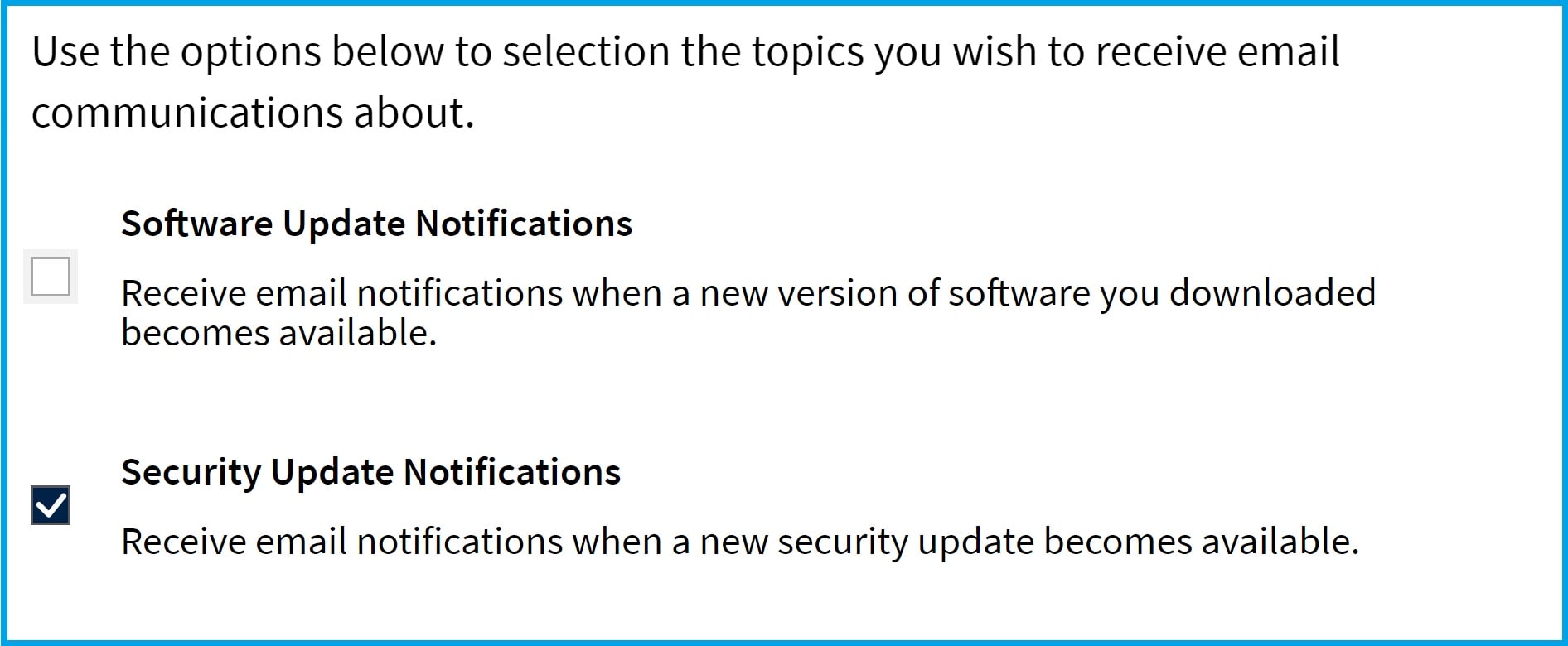
2.メール設定の管理」を選択します。

3.セキュリティ更新通知をチェック
- 発効日
- 最終更新日
概要
Supermicro、製品およびサービスのセキュリティと完全性の維持に尽力しております。本「サポート終了(EOL)セキュリティポリシー」は、サポート終了状態に達した製品のセキュリティ問題の管理方法について明示し、透明性を確保するとともに、お客様がアップグレードや移行計画を立てるお手伝いをいたします。
終末期(EOL)とは?
製品またはサービスは、開発、保守、強化が終了したことを公式に発表した時点で、EOLとみなされます。
セキュリティ・サポート・タイムライン
レガシー製品からの移行には時間がかかることを理解しています。お客様をサポートするために
- 深刻度が「クリティカル」(9.0~10.0)および「高」(7.0~8.9)のセキュリティ問題は、EOL発表日から3年間、引き続きサポートされます。
- この期間中、報告された脆弱性を評価し、重大性と影響に基づいてパッチや緩和策を発行することがあります。
- 3年経過後は、セキュリティの更新や調査は行われません。
例外
標準の3年間を超える延長セキュリティサポートは、別途契約によりご利用いただける場合がございます。詳細Supermicro お問い合わせください。
お問い合わせ
本ポリシーに関するご質問やご懸念がございましたら、セキュリティチームまでお問い合わせください:supermicro